

Share on social..
Everybody now knows that the original security measure, the simple username-password combination, has proven increasingly inadequate in safeguarding yourself online. Passwords and PINs, once the cornerstone of online security, have become vulnerable to a range of risks when used on their own.
Consequently, alternative authentication methods were needed, and Multi-Factor Authentication (MFA) was born.
These security measures include SMS/email one-time passcodes, authenticator apps, and biometric technologies like touch ID (fingerprints) and face ID on phones.
MFA security should now be a non-negotiable requirement for businesses (and individuals alike). Today, basic MFA is considered a baseline security measure, and businesses that fail to implement it across all their work applications are left exceptionally vulnerable to cyber threats.
Such is its importance, that we here at Lumina will not even offer support to a business that refuses to have MFA.
However, MFA alone is now not enough.
Inevitably, as both technology and cybercriminals have evolved, using the traditional MFA methods mentioned above are no longer enough to keep you safe. Just as the username-password combination eventually needed additional security measures around it, now too does MFA…
Methods like time-based one-time passcodes (TOTP), which generate a new security code every 60 seconds via a separate authenticator app, were considered robust due to their dynamic nature.
However, cybercriminals have found ways to bypass these measures, typically with a type of phishing attack referred to as session token theft.
In simpler terms, when you satisfy the MFA requirements and authenticate to a service (like Microsoft etc), that service creates a session token.
That token becomes your passkey for your session and as long as the token remains valid, you will not be prompted to reauthenticate. Anyone in possession of that token can access the services to which the token applies.
Imagine that you have day tickets for Glastonbury.
When you enter the festival venue, you show security your ticket, and in exchange, you’re given a special wristband. Anyone wearing the wristband can access the festival facilities and wander around unchallenged. The wristband could be taken from you without your knowledge and the thief could then also wander around the park unchallenged, as once you have the wristband, security will not ask to see the original tickets.
The Glastonbury tickets are like security measures such as the username-passwords and MFA, and the wristband is like a session token. You satisfy the security requirements (show your tickets) and are granted a session token (a wristband).
Cybercriminals can now exploit businesses by stealing these session tokens to bypass traditional MFA security measures and gain unauthorised access to sensitive company resources. Once inside, this can lead to theft of confidential data and intellectual property, and extortion.
This then poses significant risks to the business and potentially its clients as well.
It all starts with a [very convincing] phishing email.
Here is a step-by-step example of how session token theft can occur with a phishing email and a link to a document:
This type of phishing attack is often referred to as Adversary-in-the-Middle (AitM) due to the nature of the attacker acting as a ‘middle man’ between the user and Microsoft.
Session token theft allows criminals to bypass MFA because the session token that was stolen was created after the security credentials had been checked. When the session token is loaded up onto the attacker’s device, there are no MFA prompts because the session token will signal that this has already been done.
There are approximately 30 billion devices in the world today. Your system needs to know that it really is you, or anyone authorised, that is attempting to access company resources.
New phishing-resistant technologies can now help with this.
Here at Lumina, we are rolling out these new phishing-resistant security measures to all of our clients.
But what are they and how can I begin to upgrade my security?
It can, and should, be argued that the best line of defence is to continually educate your employees with consistent security awareness training.
Humans will always be the last line of defence when it comes to cybersecurity, so consistent security awareness training will never be a bad investment. However, humans are vulnerable to mistakes, even those that are well trained.
It can never be emphasised enough that no one security method is 100% hack proof, therefore cybersecurity always needs to be a multi layered approach to minimise risk.
There are multiple impactful and cost-effective solutions to combat the now vulnerable traditional MFA methods.
These solutions should be able to be implemented by your IT team.
There are a few security solutions that are phish resistant.
Passkeys represent a fundamental shift in how we protect ourselves in the digital world.
Instead of relying on passwords or passcodes that can be stolen or guessed, passkeys link your account to your specific device.
When you set up a passkey on an account:
Only a registered device can successfully login.
Creating a passkey is unlike creating a password. No secret information is ever transmitted during the login exchange, the account is only checking if the public key it has stored matches the private key on your device.
Even if someone tricks you into clicking a malicious link, they can’t access your accounts without your physical device. It’s like having a lock that only works with your specific key.
A passkey cannot be stolen via phishing.
Major tech players like Microsoft, Google, Amazon, and others have made passkeys available to all their users, and other major platforms are following suit.
This isn’t future technology – it’s here now, ready to protect your business from phishing attacks, so that you and your team can click, tap and work from anywhere without the fear of being hacked.
At Lumina Technologies, we became early adopters of passkeys, and we have already begun rolling it out to our clients.
For a comprehensive summary of passkeys and how the technology works, please click here.
FIDO security keys take the passkey measure a step further by having the same technology built into a physical security device. The main difference is that the passkeys are tied to a portable, physical security device that needs to connect to your laptop, computer, or tablet to authenticate your credentials, rather than to the device itself.
FIDO keys offer several advantages:
For a comprehensive summary of FIDO keys and how they work, please click here.
Risk-Based Conditional Access is like a smart security guard for your digital resources.
The IT system will look at factors like where a user is signing in from, what device they’re using, and their recent activity to decide how risky the login is. If it spots something suspicious, like a login from an unfamiliar location, it might ask for extra verification or even block access until it’s sure it’s really the correct user.
Rather than having static policies for everyone, the system is dynamic, and your IT Provider can create rules that require strong authentication methods for sign-ins from unfamiliar locations or devices, while allowing seamless access for low-risk scenarios.
This way, it keeps your business’s data safe by adjusting security measures based on the level of risk it detects, and without compromising user experience with countless MFA prompts and alerts.
As mentioned above, token or session cookie theft is now a prevalent hacking method used by cybercriminals to bypass traditional MFA security measures.
Token Protection serves as a vital defence mechanism against this rising threat.
The system can offer Token Protection through cryptographically tying the token to the device that created it. This means that no other device will be able to use that token.
This technology is still in its infancy and, in Microsoft’s case, currently only protects under specific scenarios. As it matures, it will become a significant protection for businesses to use under a multi-layered security approach.
Certificate-Based Authentication (CBA) operates similarly to passkeys and token protection, but it uses different technology for encryption and authentication and is centrally managed.
Unlike passkeys, which are typically generated by users themselves, certificate-based authentication involves the issuance of digital certificates by your IT team. These certificates serve to register a user’s device, or the user themselves, ensuring that only registered users or devices are permitted access to business resources. A valid certificate must be presented to successfully complete authentication and can be coupled with other MFA methods.
Certificates may be used to seamlessly connect over a VPN, access wireless networks and authenticate against company resources.
This process adds an extra layer of security to protect against potential threats and unauthorised breaches of sensitive information.
While Risk-Based Conditional Access serves as a reactive cybersecurity measure, solutions like Passkeys, Token Protection, Certificate Based Authentication, and ongoing Security Awareness Training represent crucial preventative measures. It’s imperative for businesses to implement a multi-layered approach and have both preventative and reactionary measures to achieve comprehensive security maturity.
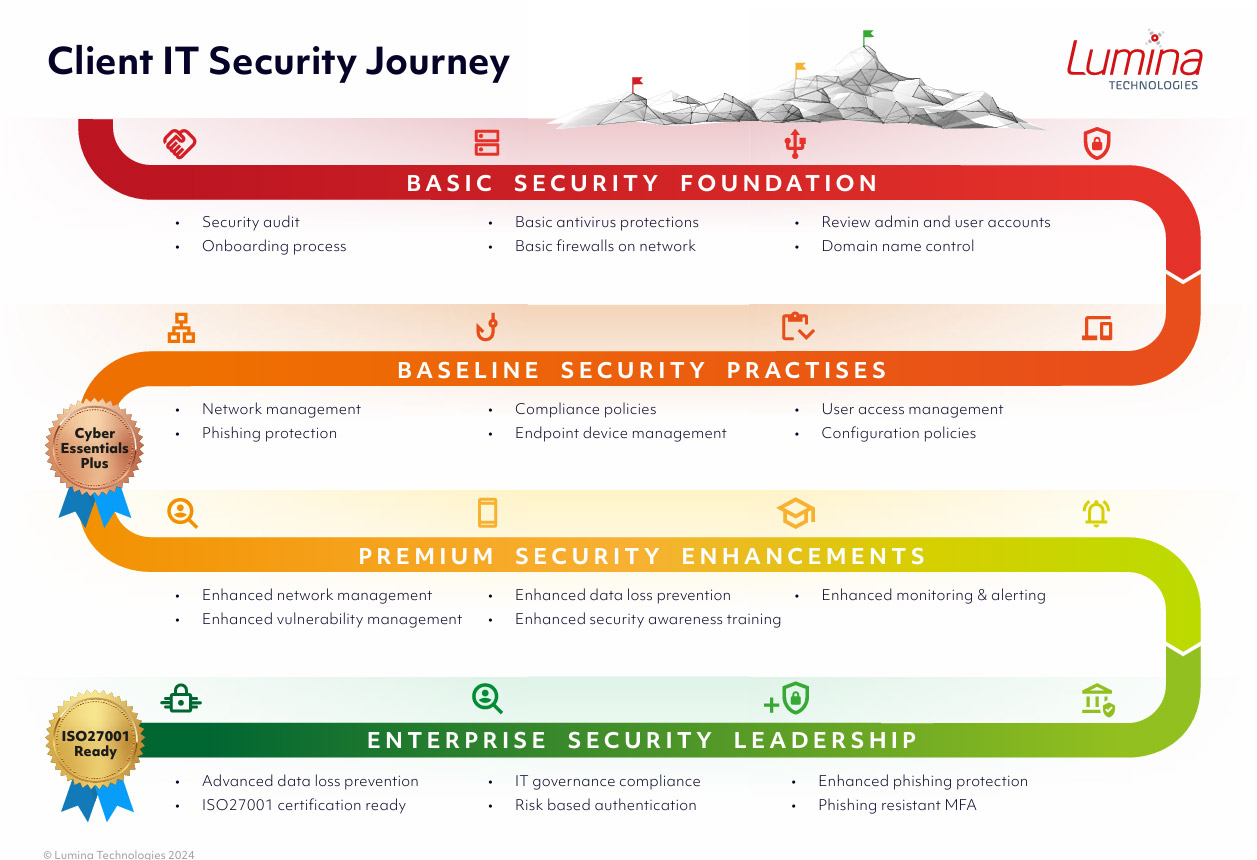
Security maturity is not a destination but a journey.
Establishing a resilient infrastructure in your business, combining technological safeguards and staff education to mitigate the risk of cyberattacks, is a gradual process that requires time and dedication.
You cannot expect it to happen overnight.
Any technology partner promising quick fixes or instant results is like a social media influencer offering a “get rich quick” scheme.
Upgrading security involves implementing additional measures beyond basic Multi-Factor Authentication (MFA).
At Lumina, we have set clear and measurable benchmarks to assess a client’s cybersecurity. This standardised approach enables us to evaluate and score our clients’ security measures accurately, providing a roadmap for continuous improvement and enhancing overall resilience against cyber threats.
What was once deemed secure, such as traditional MFA methods, now serves as a minimum baseline, highlighting the need for advanced security protocols. As technology and cybercrime evolve, new challenges arise, underscoring the importance of adaptive security solutions like those mentioned above.
While there is no 100% hack proof security solution against cyber threats, it is evident that certain measures are more effective than others. As businesses get to grips with this, it’s essential to choose security solutions wisely and pragmatically and remain vigilant in combating emerging threats.
If you would like to explore what your security journey could look like, then please get in touch by clicking the link below: