

Share on social..
Businesses are embracing technology and relying more and more on the internet for communication, and so much of what we do as part of our daily life is now online which has resulted in a massive increase in cybercrime.
Phishing continues to be the most common form of attack due its simplicity, effectiveness and high return on investment. It has evolved from the early days of tricking people with scams of Nigerian prince’s and requests for emergency medical treatment. The phishing attacks taking place now are sophisticated, targeted and increasingly difficult to spot.
Even tech giants such as Facebook and Google have suffered phishing attacks lasting more than two years in where cybercriminals posed as suppliers they regularly did business with. The criminals swindled Facebook and Google out of millions using fake corporate stamps, email addresses, and invoices.
Carbon Black reports that up to 88% of UK companies have suffered breaches in the last 12 months, and one small business in the UK is successfully hacked every 19 seconds.
There are also signs that scammers are now particularly targeting SMBs. Users of Software-as-a-Service (Saas) and webmail services are now being targeted more than any other group, according to the Anti-Phishing Working Group. This category became the biggest target for the first time recently, accounting for over a third of all phishing attacks. Around 65,000 attempts to hack SMBs occur in the UK every day, of which 4,500 are successful.
The cost to business is real and 33% of UK organisations say they have lost customers after a data breach and many UK consumers also claim that they will stop spending with a business temporarily after a security breach, and claim they will never return to a business post-breach.
Can your business afford not to take this seriously?
Phishing is a tactic used by cyber criminals that targets our businesses by sending emails that appear to be from a well-known source. It is a powerful tool, with little effort required by the criminals to steal our personal data and extort money. The sender could even be posing as the CEO or Managing Director of your company or as a business you frequently use such as Microsoft, PayPal or Amazon.
Traditionally, phishing attacks were launched through massive spam campaigns that would have targeted large groups of people. The aim was to trick as many people as possible into clicking a link or downloading a malicious attachment. There would always have been a percentage of people that clicked on the link, but as the general public has become more aware of scams, the attackers have become more sophisticated and targeted in their approach.
Cybercriminals send out fraudulent email messages that appear to come from a legitimate source. The email is designed to trick the recipient into entering confidential information (i.e. account numbers, passwords, pin numbers, birthday) into a fake website by clicking on a link. Once clicked, they can then steal sensitive information and use this to commit identity fraud or sell it on to another criminal third party, or infect a computer with malware.
Hackers use phishing to:
All it takes is for an employee to click a malicious link or attachment, enter sensitive information or fall for a false corporate email or stamp.
McAfee estimates that 97% of people around the globe are unable to identify a sophisticated phishing email so the cyber criminals are still successfully tricking people into giving away personal information or downloading malware. Despite the convincing nature of these emails, there are still some giveaway signs that may warn us of the presence of a phishing email.
Ask yourself — Do I know this person or this company contacting me?
If yes, contact the person or company by phone or by going on the company website. Do not click any links or download any attachments.
If no, see our tips below for how to spot a phishing email. If you see the signs, report the message to the email provider as spam and delete it and if applicable, warn other employees if it’s a business email domain.
Identifying a phishing email has become a lot harder than it used to be as the criminals have become much more sophisticated in their attack methods. The phishing emails that we receive in our inbox on a daily basis are increasingly well written, personalised, contain the logos and language of the brands we know and trust and are designed in such a way that it is difficult to distinguish between an official email and a fake email.
One of the first things to check in a suspicious email is the URL. If you hover your mouse over the link without clicking on it, you should see the full hyperlinked address appear. Despite seeming perfectly legitimate, if the URL does not match the address displayed, it is an indication that the message is fraudulent and likely to be a phishing email.
Example
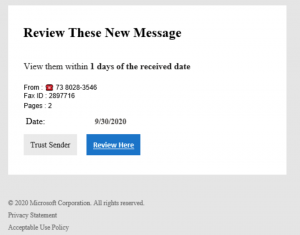
A reputable organisation will never send out an email to customers asking for personal information such as an account number, password, pin or security questions. If you receive an email requesting this information, it is likely to be a phishing email and should immediately be deleted and reported as spam.
Example
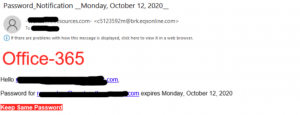
Cyber criminals are not renowned for their spelling and grammar. Whenever legitimate businesses send out emails to their prospects and customers they are often proof read a number of times to ensure the spelling and grammar is correct. If you spot spelling mistakes or grammatical errors within the email it is unlikely to have come from an official source and could indicate a phishing email.
Another common phishing tactic is to promote a sense of fear or urgency to rush someone into clicking on a link. Cyber criminals will often use threats that your security has been compromised and that urgent action is required to fix the situation. Be cautious of subject lines that claim your account has had an “unauthorised login attempt” or your “account has been suspended”. If you are unsure if the request is legitimate, contact the company directly via their official website or official telephone number.
Example
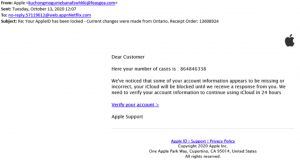
If you receive an email informing you that you have won a competition you did not enter, or a request that you click on a link to receive a prize, it’s highly likely to be a phishing email. If an offer seems too good to be true, it usually is!
Example
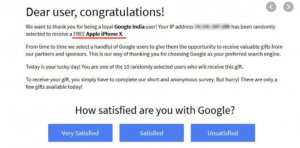
No legitimate organisation will send emails from an address that ends ‘@gmail.com’ – Not even Google! Most businesses, will have their own email domain and company accounts. For example, legitimate emails from Google will read ‘@google.com’. Look at the email address and not just the sender.
If the domain name (the bit after the @ symbol) matches the apparent sender of the email, the message is probably legitimate.
The best way to check an organisation’s domain name is to type the company’s name into a search engine.
MFA immediately increases your account security by requiring multiple forms of verification to prove your identity when signing into an application.
By providing an extra barrier and layer of security that makes it incredibly difficult for attackers to get past, MFA can block over 99.9 percent of account compromise attacks.
Anti-virus software is the first line of defence in detecting threats on your computer and blocking unauthorised users from gaining access. It is also essential to ensure that your software is regularly updated to ensure hackers are unable to gain access to your computer through vulnerabilities in older and outdated programmes.
Legitimate businesses will never send emails requesting you click on a link to enter or update personal data.
Over 90% of all successful cyber-attacks are a result of information unknowingly provided by employees. As networks become harder to attack, hackers are increasingly targeting what they perceive as the weakness in a company’s defences – its employees!
Companies may have the strongest of cyber defence systems in place, but these systems offer little protection if cyber-criminals are able to bypass these traditional technological defences and get straight to an employee tricking them into giving out sensitive information.
As hackers hone their techniques and become more targeted in their attacks, it’s important to educate staff and provide regular training on what they should be looking out for and how they can play their part in preventing a phishing attack.
The internet and social media has transformed how we communicate with each other on a day to day basis, however this culture of sharing has provided cyber criminals with an easy way to profile potential victims ensuring their phishing attempts are more targeted and harder to spot.
Hackers are turning more and more to social media platforms to access personal information such as age, job title, email address, location and social activity. Access to this data provides the hackers with enough info to launch a highly targeted and personalised phishing attack.
To reduce your chance of falling for a phishing email, think more carefully about what you post online, take advantage of enhanced privacy options, restrict access to anyone you don’t know, and create strong passwords for all your social media accounts.
Before entering any information into a website, you should always check that a site is safe and secure. The best way to do this is to look at the URL of a website. If it begins with a “https” instead of “http” it means the site has been secured using an SSL Certificate. This ensures that all your data is secure as it is passed from your browser to the website’s server. There should also be a small padlock icon near the address bar which also indicates the site is secure.
Lumina Technologies offers advanced cybersecurity solutions to protect businesses and their employees from falling victim to phishing emails, as well as keeping software patched and secure.