

Share on social..
Cyber security isn’t optional for businesses today – it’s a necessity. Unfortunately, many small-medium sized businesses and enterprises (SMEs) are not adequately secure. This poses a major issue as the data shows that SMEs are the most targeted organisations by cybercriminals.
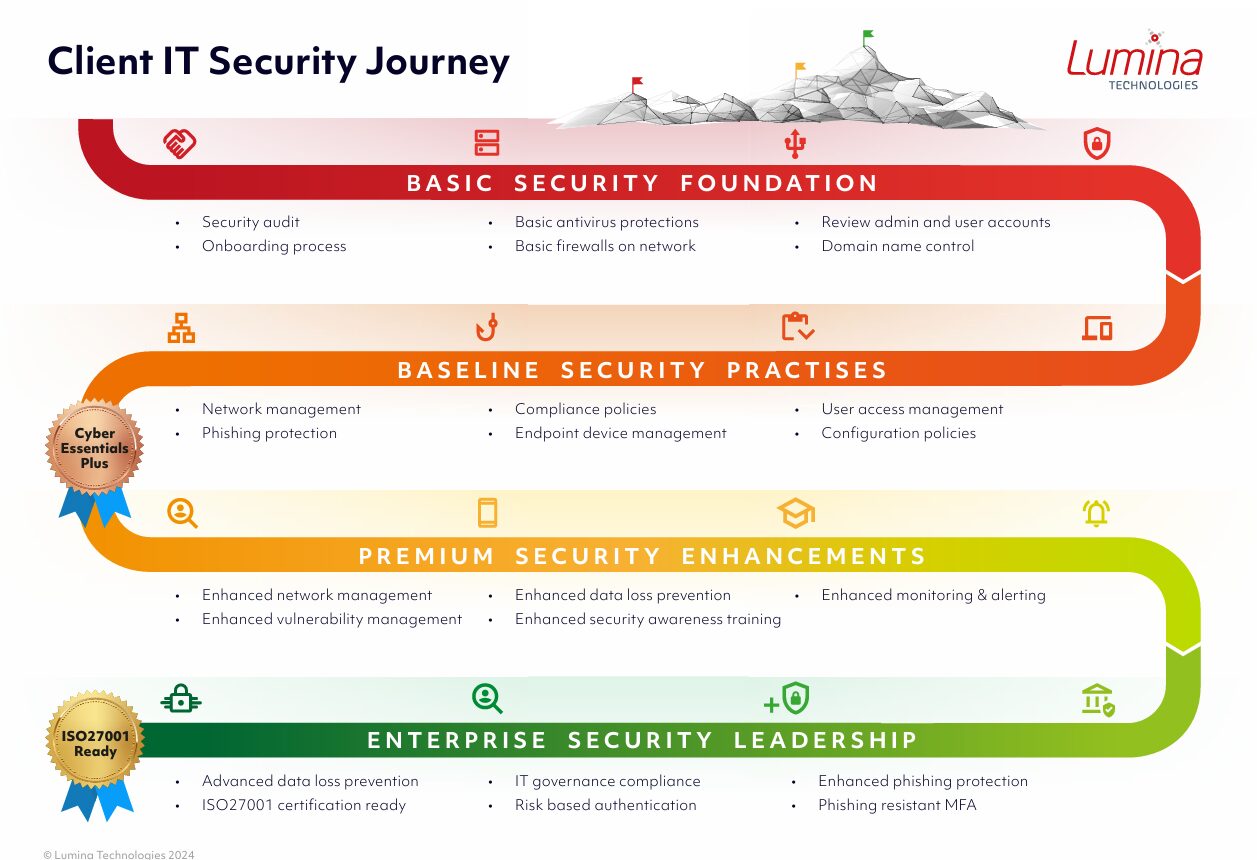
But where do you start so you can understand whether the protective security measures you have in place are sufficient?
Getting Cyber Essentials certified can be a good place to start, especially as more commercial and government contracts are now expecting it as a baseline level of cyber security. In fact, 13% of businesses obtained Cyber Essentials specifically for government contracts, with another 13% requiring it for commercial contracts.
Cyber Essentials, a UK government-backed self assessment scheme that can guide many organisations, including SMEs, to a cost-effective way to implement basic cyber defences.
This blog will outline why Cyber Essentials is valuable and why your business should consider it as a starting point in your cybersecurity journey. We’ll cover the Cyber Essentials requirements and how your business can implement them.
Cyber Essentials is a UK government-backed scheme that provides a framework for businesses to install good cyber hygiene practices, so that organisations can protect themselves against the most common cyber attacks.
Think of it as a digital health check-up for your business.
It’s important to note that Cyber Essentials accreditation only lasts 12 months from the date of issue. This means that achieving Cyber Essentials certification is not a one-and-done process, and the security protocols need to be kept in place for successful renewal each year.
There are two tiers to a Cyber Essentials certification process:
1.Cyber Essentials (Basic Level)
A self-assessment option that protects against common cyber attacks.
Why is it important?
2.Cyber Essentials Plus (Advanced Level)
An enhanced version of Cyber Essentials with hands-on technical audit.
Key differences:
To put it simply, the basic level (Cyber Essentials) is like having a lock on your door, while the advanced level (Cyber Essentials Plus) is like having that lock checked by a professional locksmith to ensure it’s properly installed and working correctly.
Cyber Essentials infrastructure requirements focus on five controls:
Let’s break down these Cyber Essentials requirements.
A firewall acts as a digital security guard for your devices and networks. It controls what information can come in and go out, helping to protect against common cyber attacks. Imagine your computer or network as a house. A firewall is like having a smart door that only lets in invited guests and keeps out strangers.
Firewalls can be used on many things:
To meet Cyber Essentials certification requirements, you need to:
Secure configuration is about setting up computers and network devices safely. Many devices come with default settings that can be a weak points for attackers. The goal is to reduce vulnerabilities on each user’s device and only keep necessary services running. This is a crucial part of the cyber essentials infrastructure requirements.
The default configurations that are considered weak points include easy-to-guess default passwords that aren’t changed by the user or preinstalled apps that aren’t needed and may pose an exposure risk to cyber attacks.
To meet Cyber Essentials certification requirements, you need to:
User access control is about managing who can access certain types of company data. It’s like having different keys for different rooms in a building.
You want to have technical controls to make sure only authorised people can enter specific areas of stored data.
To meet Cyber Essentials certification requirements, you need to:
Malware is harmful software designed to damage or gain unauthorised access to your systems. It includes viruses and ransomware. Without sufficient protection, you risk system malfunctions, data loss, and the spread of malware to other devices.
Malware can appear on your device through clicking on an email attachment from an attacker, downloading an infected app, by accidentally (or being tricked into) using malicious websites, or downloading it directly onto your device.
To meet Cyber Essentials certification requirements, you need to:
Keeping your software and devices up-to-date is crucial for protecting against known security issues and the most common cyber attacks. It’s like maintaining your home’s security system – it needs regular attention to keep you safe. This is another key aspect of the cyber essentials infrastructure requirements.
Devices will include desktops, laptops, phones, tablets, networks, approved applications, and cloud services.
To meet Cyber Essentials certification requirements, you need to:
While Cyber Essentials provides a solid foundation for cyber security, small businesses should seriously consider opting for Cyber Essentials Plus. This advanced certification offers a better defence against cyber threats. With Cyber Essentials Plus, you’re not just ticking boxes; you’re getting an independent verification of your security measures through a hands-on technical assessment.
This thorough evaluation can uncover vulnerabilities and security controls that might be missed in a self-assessment questionnaire, providing you with a more comprehensive view of your cybersecurity position. This attention to detail is proving effective – the failure rate for Cyber Essentials has dropped for the third straight year to just 2%.
Moreover, Cyber Essentials Plus sends a stronger signal to your clients and stakeholders about your commitment to data protection. The numbers speak for themselves – organisations with Cyber Essentials are 92% less likely to claim on cyber insurance policies.
With the increasing number of breaches happening to businesses today, this enhanced credibility can be a significant competitive advantage. It’s no surprise that 89% of certified organisations would recommend Cyber Essentials to others like theirs, with 91% planning to recertify next year.
To reiterate, cyber security is no longer optional – it’s essential for businesses of all sizes. Cyber Essentials, or Cyber Essentials Plus provides an excellent starting point for SMEs looking to enhance their cybersecurity measures and gain a competitive advantage.
As more organisations are now focusing on their supply chain security, a Cyber Essentials certificate is now expected as a baseline to secure big commercial and government contracts – so you don’t want to automatically disqualify your business by not having it.
A trusted IT provider can help take the burden off you and help you achieve and maintain your certification. They can guide you through the process, implement the cyber security measures, and ensure your operating systems remain compliant with Cyber Essentials requirements year after year.
Click Here to Contact Us about Cyber Essentials.
Sources: