

Share on social..
As a small precision engineering firm, have you ever considered that your cybersecurity practices could make or break your relationships with major clients?
Supply chains in manufacturing have always been complex and niche oriented. Consider Rolls Royce, the luxury car manufacturer. To create their iconic vehicles, Rolls Royce relies on a vast network of specialised suppliers – from small precision engineering firms crafting engine parts to electrical engineers designing sophisticated circuit boards for the electrical components. Each of these suppliers, while experts in their field, represents a potential weak link in Rolls Royce’s supply chain.
Why?
Because these smaller, niche firms often lack the robust cybersecurity measures of their larger counterparts. Hackers are increasingly carrying out supply chain attacks by using these smaller suppliers as backdoors into larger, more secure organisations.
According to the UK government’s 2024 Cyber Security Breaches Survey, half of all businesses experienced some form of cyber security breach or attack in the last 12 months, with the average cost of disruption ranging from £1,200 to £10,000.
As cyber attacks grow increasingly sophisticated, larger companies must now be vigilant and enforce supply chain security. The interconnectedness means that a breach anywhere in the supply chain can have far-reaching consequences.
In this blog, we’ll explore the five biggest cybersecurity risks you face as a small supplier and provide practical steps for your own supply chain management.
Let’s start by addressing the elephant in the room – your potential role as a weak link in the supply chain.
As a small precision engineering firm, you’re not just a cog in the machine – you’re a critical link in a complex supply chain. Large corporations, whether they are in the automotive, defence, or aerospace industries, often rely on smaller, specialised engineering or sheet metal firms as part of their supply chain network. While you provide these organisations with invaluable expertise and quality, you also represent a potential weak link in their supply chain security that cybercriminals exploit.
Imagine being the firm that inadvertently leaks the latest Formula 1 engine design. The fallout would be catastrophic – not just for the racing team, but for your business too. A compromise like this would not only impact the reputation and financial stability of the Formula 1 company, but also that of your own firm.
As a small engineering firm, it’s crucial to recognise that you sit somewhere in a supply chain, even if it’s not immediately obvious. You’re one of the links in the chain to a much larger organisation who, in turn, will begin vetting their suppliers, if they are not doing so already. Ultimately, there will be a chain reaction where each supplier will pass on the burden of responsibility for ensuring cybersecurity within the supply chain.
Larger companies are leading the charge in demanding accountability from vendors and their suppliers. They’re starting to require proof of adequate cybersecurity measures to protect their intellectual property and confidential data.
This trend will inevitably filter down the supply chain, so it’s time to prepare yourself.
As larger companies begin to crack down on their supply chain security, failing to meet certain compliance or basic cybersecurity standards can quickly become very damaging to engineering firms.
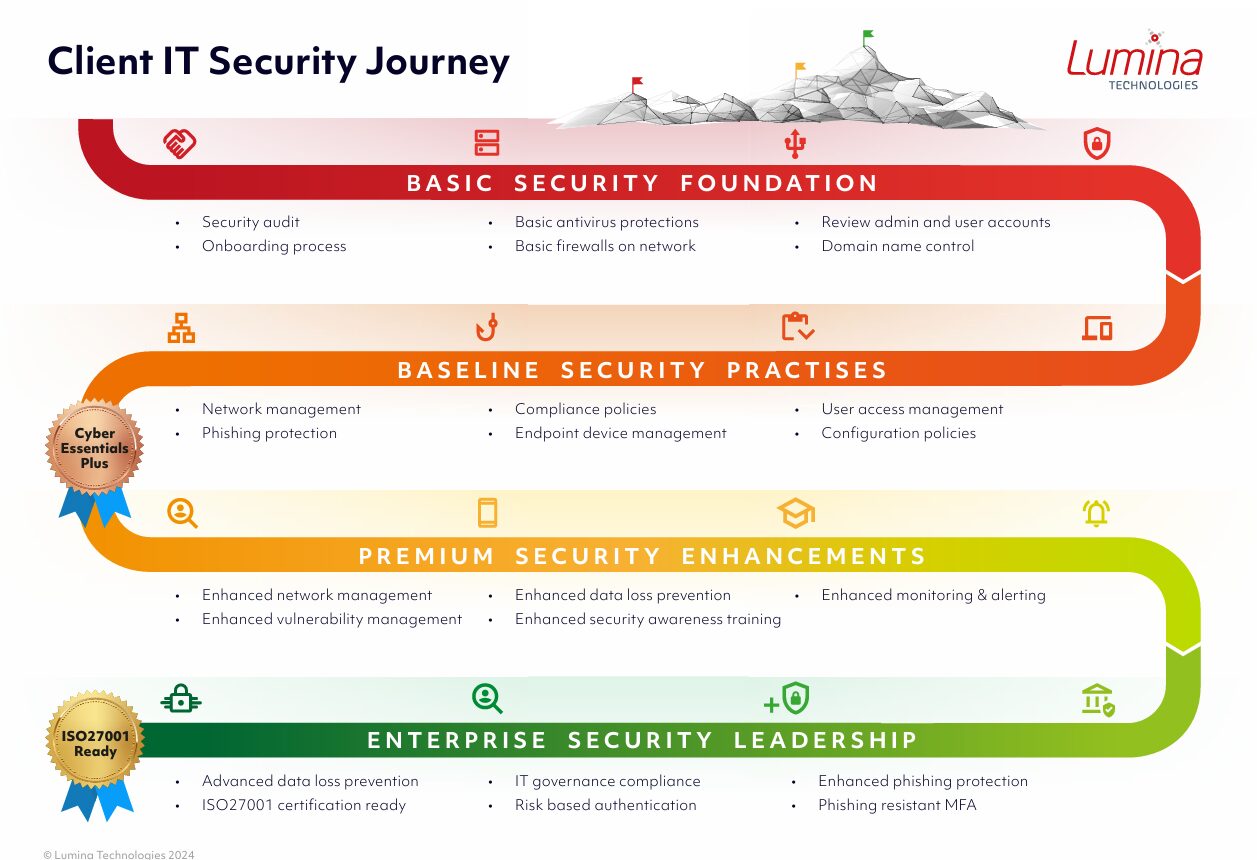
As a small firm, achieving certifications like Cyber Essentials might seem daunting, but it’s increasingly becoming a prerequisite to working with larger clients (or to continue working with them).
Take St James’s Place, one of the UK’s largest wealth management companies. In 2024, they required their network of over 2,800 independent businesses to certify to Cyber Essentials Plus.
The result? An 80% reduction in cybersecurity incidents across their supply chain.
Additional government data show that Cyber Essentials is growing rapidly.
Over 33,000 certifications were issued in 2024 – a 20% increase from the previous year.
This growth reflects its increasing importance in supply chain security. This is unsurprising when you consider that organisations with this certification are 92% less likely to claim on cyber insurance policies.
Non-compliance can result in lost contracts, damaged reputations, and increased vulnerability to supply chain attacks due to subpar security measures.
A proactive risk management strategy is key to addressing this issue.
Working with a reputable IT partner can help you to stay informed about relevant compliance requirements and obtain any necessary certifications. An IT partner can also help with regular internal audits that can help identify and address potential security gaps before they become liabilities in your organisation or supply chain network.
Here is another supply chain threat that may feel awkward to address – aging equipment like your CNC milling machines.
It’s not unusual for engineering firms to rely on legacy systems or outdated software, especially for users of specialised equipment like Trumpf or DMG laser and CNC machines. Many of these machines run on embedded operating systems that were programmed to run on Windows XP, an operating system that Microsoft no longer supports. These embedded operating systems on the machines cannot be updated with new software, which poses both a security and financial conundrum.
It’s usually not feasible or realistic for an engineering firm to upgrade and buy brand new machines. Therefore, it’s very normal for firms to make do with a mixed bunch of outdated operating systems on the machines.
But how can IT keep them safe and continue to be operational?
To mitigate this risk, work with your IT partner to create ‘safe zones’ for your legacy equipment and its outdated software. It’s like creating a secure vault within your network where these vulnerable machines can operate without putting your entire system at risk.
Your IT partner can work with you to implement strict access controls and network segmentation to isolate vulnerable systems from the rest of the supply chain network. For instance, creating a separate network for CNC machines with limited communication to the main business network can significantly enhance supply chain security.
There is still a risk as the machines are still vulnerable to being compromised via the Windows PC that operates them, but by isolating the network, the risk is greatly reduced.
Your machines aren’t the only valuable assets at risk. Also at risk is arguably the most important component for a precision engineering firm – your intellectual property (IP).
Intellectual property theft for small precision engineering firms tends to be two-fold. There is the risk to your own CAD designs, if you engineer them, and the threat to client property. Inadequate protection of this proprietary information can lead to theft, resulting in loss of competitive advantage, financial losses, and potential legal issues if client data is compromised.
Imagine waking up to find your proprietary designs are being manufactured halfway across the world, undercutting your business. This nightmare scenario is all too real for many small engineering firms.
Consider the case of a precision engineering firm working on components for a new aircraft engine. The firm’s CAD designs and manufacturing processes represent years of research and development. If these were to fall into the wrong hands due to a supply chain attack, it could not only compromise the firm’s competitive edge, but on a much more serious note, could also potentially impact national security if the IP were for military use.
To safeguard IP, work with a trusted IT partner to develop and implement strong data classification policies, access controls, and encryption methods. Additionally, carefully assess your own third-party vulnerabilities and monitor your suppliers and their access to your sensitive information to help reduce third-party risks on your end, as well as keeping the IP of your larger clients safe.
For instance, implementing a system where any sensitive data and design files can only be accessed on specific, highly secure workstations can significantly reduce the risk of data theft within the supply chain.
All these risks point to one overarching issue – the need for proactive cybersecurity.
The clock is ticking.
With the threat of a cyber attack always looming, every day without robust security measures is a day you’re gambling with your employees and your business’s future.
The 2024 government data reveals that only 31% of businesses have undertaken cyber security risk assessments in the last year.
The reality for small precision engineering firms is that you are sitting on a ticking time bomb if you are not being proactive in your cybersecurity. A reactive approach, where firms only address issues when forced by client demands or after an incident occurs, leaves you vulnerable to emerging threats in the supply chain.
What happens if you have a large commercial contract with the UK defence industry, and one day they demand that unless you have achieved Cyber Essentials certification within a certain timeframe, say 90 days, then they will pull the contract with you?
Where will this suddenly leave you?
This scenario is becoming increasingly common. The pressure of such client demands is likely to intensify when the realisation hits that it isn’t as simple as originally thought to become Cyber Essentials certified.
The process often involves some IT project work to bring your cybersecurity in line with the supply chain requirements, depending on how mature it is to begin with. If you are a firm that has very little protection in place, then there is a chance that it may take longer than the set deadline to achieve Cyber Essentials.
To combat this risk, adopt a proactive stance on cybersecurity.
Work with the right IT partner that will set up the right infrastructure for your business needs, regularly update security protocols, and conduct frequent account meetings to keep you up to date and hold you accountable.
Having an effective strategic IT partner can significantly improve your firm’s ability to prevent and respond to cyber attacks within your supply chain management processes.
As a small precision engineering firm, you’re not just crafting components – you’re forging critical links in a wider supply chain. The cybersecurity risks we’ve explored aren’t just abstract threats, they’re very real challenges that you’ll likely encounter sooner rather than later.
But here’s the good news: by taking proactive steps to address these risks, you’re not just protecting your business – you’re positioning yourself as a trusted, secure partner in an increasingly security-conscious industry.
Implementing robust security measures, achieving relevant certifications, and working closely with a knowledgeable IT partner isn’t just a risk management strategy – It’s a strategic investment in your firm’s future.
Remember, in today’s interconnected world, your cybersecurity isn’t just about you – it’s about every client you serve and every supply chain you’re part of.
By prioritising your security today, you’re not only safeguarding your business but also opening doors to new opportunities and partnerships.
Don’t wait for a crisis or a client ultimatum to act. Take the first step today.
Assess your current cybersecurity posture, reach out to a trusted IT partner, and start your journey towards becoming not just a supplier, but a secure, indispensable link in the global manufacturing chain.
Lumina have created an IT security roadmap for engineering firms who want to enhance their supply chain security and achieve certifications such as Cyber Essentials.
Click Here to Contact us Today!
Sources: